After visiting the European Christmas Market we walked over to the Glow Holiday Festival at CHS Field. It was fun to walk amongst all the lights and there were many activities.





We had a great time visiting the St. Paul European Christmas Market tonight. We had delicious food and checked out many different shops.




We attended our first St. Olaf Christmas Festival at Orchestra Hall. This year was themed Love and Joy. This concert has been held since 1912. The mass choral arrangements with all 500 students were wonderful. Orchestra Hall was the perfect venue as well.

First time stopping at Smith Coffee & Cafe and was very impressed with their coffee program and the pastries were great.

In celebration of our niece’s 16th Birthday she arranged a large group of family and friends to go to Feed My Starving Children and pack food this morning! Our group packed 42 of the 180 boxes for the session, for a total of 38,880 meals. It was a fun time doing good!

New Standards Holiday Show 2023
We had a fun night at the 2023 New Standards Holiday Show tonight! This is a holiday tradition of ours and is always a fun evening. There were many returning and new special guests. The show wrapped with the excellent Christmastime Next Year. 🎄



New Standards Holiday Shows: 2023, 2021, 2019, 2018, 2013, and 2012.
Cyber Monday 2023! 🚀

What is your favorite iPhone?
The other day Alex stopped by my office and asked me “What is your favorite iPhone that you have owned?” My first reaction was that sure is a random question and then it got me thinking. What was it? I gave him a quick answer and then thought that would be a fun blog post. So here we are. I couldn’t just give one, for me there are three that stand out.
- iPhone: Yeah, the first one. I stood in line at Southdale Mall outside the Apple Store to get it. I was excited by the device and felt like it was going to be a “game changer”. I wanted to have the first one on the first day so that I could experience the entire journey.
- iPhone 4: I upgraded to this one and the new design with less curved edges appealed to me. This phone also had the first retina display and it was the first one with a front facing camera. I also upgraded to iPhone 4s to get a little speed boost.
- iPhone Xs: I enjoyed the iPhone 7 with its button-less button, but when I upgraded to iPhone Xs I loved the removal of the home button. I remember thinking it would take some time to get used to, but it didn’t. The gesture interface that is now on all phones was an instant hit.
Also, since we’re on the topic of iPhones, here is a complete list of iPhones I’ve owned. I initially bought each successive generation, and then moved to upgrading every two years. Now probably every three years. The quick jump from the 13 Pro to 14 Pro was to hand our phones down to our kids. Links are all to the Wikipedia page for each one.
Things 4 Good 2023 Fall Fundraiser Insights
We had a great time hosting our 3rd annual Things 4 Good Fall Fundraiser. We raised nearly $6,000 in donations for our four non-profits. A fun thing for me about the fundraiser is it lets us play the role of a retailer for a weekend.
This year we had 55 candle purchases which compares to 52 in 2022 and 51 in 2021. On average people purchased 4 candles. However averages don’t always tell the story. Most people get two candles, and then there are a smaller number of people that get a large number — usually as gifts for the holidays.
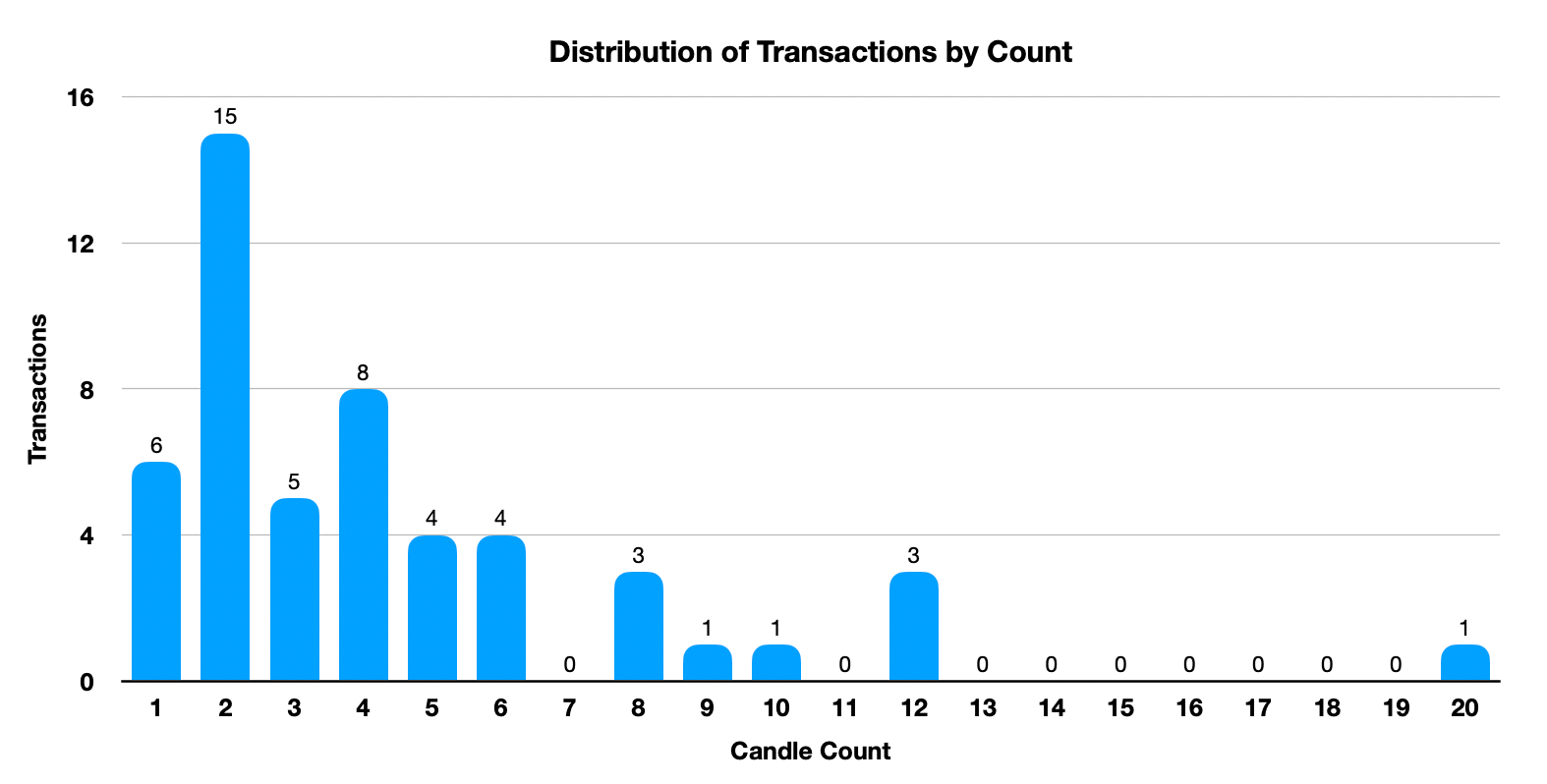
We had some new scents this year, and had more scents than we have had the previous two years. The first year we had only four scents, and last year six. This year we had eight different scents. As the number of scents go up we need to be more planful with inventory. For the first time this year we tracked which scents people picked so that we could get better insight for future years. Here is a look at rolling inventory.
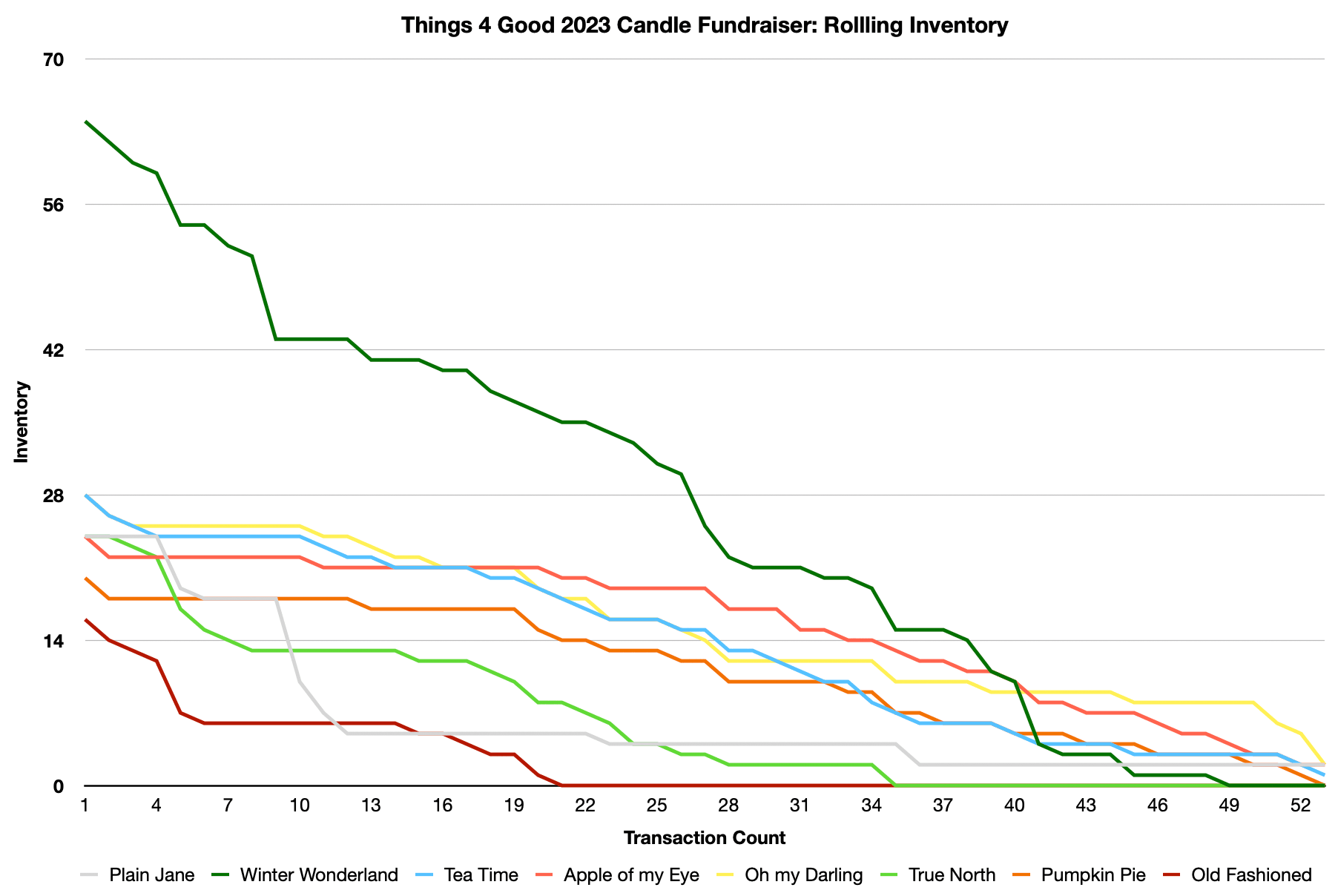
Some observations:
- Winter Wonderland is always the most popular scent and we started with more than twice as many of those as any other scent.
- Old Fashioned was a very popular new scent this year and was the first to sell out.
- Plain Jane, also a new scent, had a lot of early sales and then slowed down a lot. This scent was most popular when someone bought a lot of candles as gifts.
I fed the transaction data into ChatGPT and used its data analysis mode to make a run at doing inventory planning for next year. It did a reasonable job but with such a simple dataset I could have gotten most of the way there on my own. It recommended a 30% increase for True North and 20% increase for Old Fashioned. Even though it was a simple use case, it highlighted how powerful it could be at that use case.
We offer folks a number of ways to donate and again Venmo was by far the most popular method, twice as popular as cash. I’ve offered the ability to pay with crypto for all three years, and this year we had our first donation made with Bitcoin via the Lightning Network!
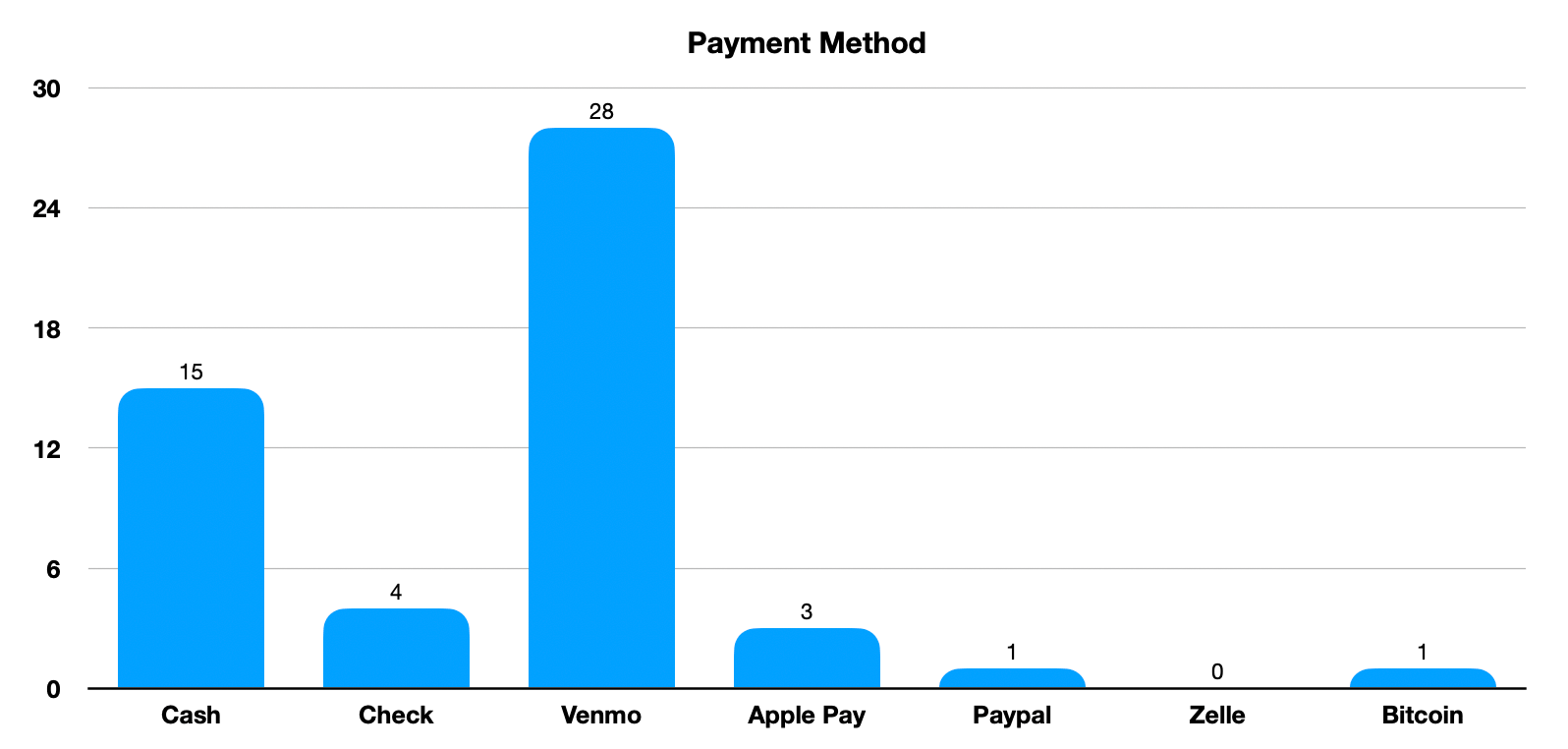
Interesting data for us which will help us with next years event. We are already keeping notes for things we want to do to make next year’s Things 4 Good Fall Fundraiser even better. Send us an email if you have any suggestions!
Also see 2023 Fall Fundraiser Results.
Watched Elf tonight! Tradition of ours every year right after Thanksgiving. This viewing was one of my favorites. What a great movie! 🎬🎄

A friend shared this powerful maxim with me. I have found it useful in recent conversations.
Does the question need to be asked?
Does the question need to be asked now?
Does the question need to be asked by you?
I’ve been surprised at how frequently I come to a “no” for one of these questions. 🤔
I made my traditional Christmas season Toffee Bars today. My Grandma Rose always had these freshly made at the farm when we visited. Her and my Mom have made hundreds of pans of these over the years. Tradition.

Tyler’s Christmas Twinkle Lights had a break in the wiring. Gave me the opportunity to get the soldering iron out. Working now! 💡


We got our Christmas Tree at Gifford’s Tree Farm in Lakeville today. We found a wonderful 10’ tree that is just right!



Happy Thanksgiving!
OpenAI Rewind: New Board, Altman Returns ⏪
Wow. First OpenAI…
We have reached an agreement in principle for Sam Altman to return to OpenAI as CEO with a new initial board of Bret Taylor (Chair), Larry Summers, and Adam D’Angelo. — OpenAI
Then Sam Altman…
i love openai, and everything i’ve done over the past few days has been in service of keeping this team and its mission together. when i decided to join msft on sun evening, it was clear that was the best path for me and the team. with the new board and w satya’s support, i’m looking forward to returning to openai, and building on our strong partnership with msft. — Sam Altman
Then Satya Nadella…
We are encouraged by the changes to the OpenAI board. We believe this is a first essential step on a path to more stable, well-informed, and effective governance. Sam, Greg, and I have talked and agreed they have a key role to play along with the OAI leadership team in ensuring OAI continues to thrive and build on its mission. We look forward to building on our strong partnership and delivering the value of this next generation of AI to our customers and partners. — Satya Nadella
All messages posted in a 6 minute period. Is Humpty Dumpty together again?

DALL-E rendition of Satya Nadella and Sam Altman celebrating after successfully putting Humpty Dumpty back together.
Related Links
If you want to read more than you really ever could justify reading about this.
- Foundational Risks of OpenAI – On my Om
- More on Sam Altman’s Sudden Departure from OpenAI – 512 Pixels
- Details emerge of surprise board coup that ousted CEO Sam Altman at OpenAI | Ars Technica
- Daring Fireball: More on Sam Altman’s Ouster From OpenAI
- OpenAI announces leadership transition
- Microsoft hires former OpenAI CEO Sam Altman - The Verge
- How ChatGPT Fractured OpenAI - The Atlantic
- OpenAI’s Misalignment and Microsoft’s Gain – Stratechery by Ben Thompson
- Daring Fireball: OpenAI Drama Continues
- Even After Freaky Friday, Microsoft is Still the AI King – On my Om
- OpenAI drama is over. – On my Om
Prediction: Microsoft will acquire OpenAI
I’ve been following the self-created chaos at OpenAI since Friday’s shocking announcement that the OpenAI board fired Sam Altman. I thought it was a made up headline at first, probably AI generated. My son asked me what I thought would happen and there were three paths I felt were likely.
- Every venture firm in Silicon Valley would be offering blank checks to Altman to create a new AI company not limited by the non-profit aspects of OpenAI.
- Satya Nadella at Microsoft would offer Altman to join Microsoft and lead all things AI with an unlimited investment budget.
- OpenAI would hire Altman back because they can’t move forward without him.
On Sunday night Nadella announced Altman was joining Microsoft, along with others. Option 2 seems to be the choice.
However, now we know that Altman hasn’t signed any agreement with Microsoft. We also know that 700 of 770 employees at OpenAI have requested the board to resign and for Altman to return.
The OpenAI board seems to be fairly clueless here. With the firing of Altman, they effectively pushed Humpty Dumpty off the wall and broke OpenAI into pieces. I suspect that right now Nadella and Altman are the ones trying to figure out how to put it back together again. And I suspect there is only one real option:
Prediction: Microsoft will acquire OpenAI.
- Altman can’t be two places1.
- Microsoft is a big investor and partner in OpenAI.
- There would be collateral damage to letting OpenAI fail.
In the end Nadella wins in every dimension here. He ends up being the adult in the room putting Humpty Dumpty back together. Altman continues as the visionary AI leader he is. OpenAI remains as a strongly recognized brand. The OpenAI board is dismissed and noted for smashing the bottle after they captured lightning in it.2
-
Yes Jack Dorsey led Square and Twitter and Elon Musk leads multiple companies. I’m doubtful Altman ends with two roles, leading OpenAI and at Microsoft? Seems unlikely but is possible. ↩︎
-
OpenAI’s rather unique governance structure with a non-profit at the heart of it makes this more complicated, but I don’t think impossible. ↩︎
We had a great time seeing my nephew Andrew Keating perform in Matilda Jr. at the Reif Center. He played the role of Mr. Harry Wormwood, Matilda’s mean father. He did a great job as did the entire cast. Andrew was even asked for his autograph on the playbill!


While having dinner at Rapids Brewing we got to hear the beginning of Grant Glad’s set and I liked what he was playing a lot. 🎶

