Crypto
Forays into blockchain, NFTs and POAPs live here. I write about minting POAP tokens at family events, celebrating Ethereum’s 10‑year anniversary by creating an NFT and even using monitoring services to keep my POAP feeds up and running.
- Todd Van Nurden, Principal Developer Cloud Architect and Mad Scientist, Microsoft Technology Center’s
- Sam Pierson, Chief Technology Officer, Talend
- Tammylynne Jonas, Global CIOGlobal CIO, Donaldson
- Why now? AI has been in the works for a long time. Has there been a technological breakthrough recently?
- How does Generative AI affect how we build software.
- How does Generative AI benefit from these early releases.
- Opportunities technologists see to use this capability in their organizations.
- What are some of the risks to keep an eye on?
- AI as a coach or mentor?
- Easy to parse list of upcoming community events
- No more than three relevant links to news about the tech community
- Community Supporter Highlight, randomly share a bio about one of the community supporters each issue
- Project Highlights from Community Supporters to submit and share a project (personal, hobby, business) that they would like to highlight for everyone
- re(center)ed which provided an opportunity for people to write a message on a piece of wood and then hang it anonymously on the wall. Every few hours the curator would pull them down and burn them in a “pyre”, releasing the sentiment.
- Archive of Collective Memory that allowed you to submit a message via the web that was then turned into an audio loop and played through a wooden wall that you had to put your ear against to hear it.
- Blankets of Ice which had a bedroom set in the middle of the snow with a “quilt” pattern made of colored ice blocks.
- Chapsicle of Love provided marriage service at the event.
- Techno From the Sun was a shanty powered only by solar energy with people DJ’ing techno music inside. You could modify and add to the mix by moving levers and dials on the outside of the shanty.
- On-chain analytics, how close am I to POAP.eth via POAPs?
- Add annotation to each POAP so I can fill out the memory more.
- Notify me of POAP drops “around me”
- Notify me of any POAP Deliveries waiting for me.
- Credit for 1 mainnet migration a month.
- Issue POAP by email address, hide claim codes entirely from everyone.
- Collections/series of POAP.
- Integration with my analytics service, so embed my Phantom Analytics or other tracking code.
- Support for external identifiers in claim codes so I can embed an identifier to my systems.
- Post-claim redirect.
- Additional metadata added to each claim
- White Label claim page
- Design services, POAP specific look
- Priority support, will hit your deadline
- Assistance with claim code distribution
- Everything in POAP Pro.
- 2 Studio events a year included.
- Would need something more.
- PAOP Pro for free
- 1 Studio events a year
Minnebar 17 POAPs
I am excited to share that all attendees to Minnebar 17 will be getting a POAP token! In addition to the traditional t-shirt, there will be a unique claim code given to everyone so that they can claim a permanent collectible from the event. 🎉
What is a POAP? Technically it is an NFT that is issued as a collectible for an event or occasion. It is like a digital version of a sticker or shirt. I’ve collected over 80 of them, see my collection for some examples.
POAP is pronounced “poh-ap”.
Update: Also see the Minnebar 17 StayNftyMpls 612 Series Giveaway!
The POAPs
There will actually be three POAP tokens given at Minnebar 17. 🤩
Attendee: All attendees will be given a claim code when they check in on arrival. Everyone that attends will get one of these.
Presenter: All presenters that sign up via the Sessionizer will have a claim code sent to them.
Organizer: All organizers who help put the event on will have a claim code sent to them.
Any holder of these POAPs will also be eligible to enter into a raffle at no cost to win something special. Stay tuned for more information on that!
I also plan to have my personal You’ve met thingelstad.eth tokens ready for distribution. Ask me for one at the event. 😊
How to get ready?
If you want to get ready ahead of time so that you can claim these easily you can do two things.
First, you need an Ethereum wallet and address. If you don’t have one, I highly recommend using Rainbow on iOS or Android. It is a very well done wallet and is simple to setup and get started with. It is totally free.
Once you have an address you are ready to go, but if you want to make it even easier you can install the POAP App too. This is also available on iOS and Android. If you configure this with your wallet address you can automatically claim a POAP just by scanning a QR code or tapping an NFC device.
Questions
What is a POAP?
POAP stands for Proof of Attendance Protocol. The POAP website has a good explainer. Functionally they are ERC-721 tokens issued on the Gnosis blockchain. The smart contracts for POAPs have a number of additional applications built around them to add additional utility.
How much does this cost?
Nothing. No funds or crypto are required to collect as many POAPs as you want. All gas fees for minting the POAPs are covered by POAP.
What is the environmental impact?
POAPs are issued on the Gnosis blockchain which uses a proof-of-stake validator mechanism similar to modern Ethereum. As such, it uses minimal power.
Can I sell the POAP?
POAPs are meant to collect and curate memories, not make money. It is strongly discouraged to sell a POAP, but technically you can. As an ERC-721 NFT you can send POAPs from one wallet to another on Gnosis chain. You can also migrate the POAP to Ethereum mainnet, however there is a 0.1 ETH fee for doing that which is largely intended to keep people from attempting to sell them.
Why do some POAP owners have names?
POAPs are held by wallets, and if you buy and configure an Ethereum Name Service name the wallet address can be displayed as a name. If you would like to do this, go to the ENS app and buy your preferred name, remember to set the reverse address lookup, and your name will be shown instead of an address.
If you have other questions, check out the POAP Help Center.
Transferring NFTs in Bulk
After I created additional Ethereum addresses for specific applications, I wanted to move existing assets to align with that.
Ethereum Name Service
Moving ENS names is a special case. The ENS address is itself an NFT, but you cannot just send these to another address. You can move them, but you have to do it in the ENS application. For each of the 21 ENS names I have I did an on-chain transaction to move them to ens.thingelstad.eth. It was easy to do, and even though there was no bulk operation it wasn’t hard to do. Each move incurred some gas fees.
POAPs and NiftyInks
With over 70 POAPs to move I really didn’t want to do these by hand. And with over 730 Nifty Inks it was out of the question to do it by hand. I looked at how to move POAPs and the FAQ recommended uNFT Wallet. I connected my wallet via Gnosis Chain and uNFT Wallet already had the contract address for POAP and Nifty Ink. I was able to move most of my POAPs with one transaction and a second after doing a test. They are now in POAP.thingelstad.eth.
I had never transferred POAPs between accounts and it is interesting that these now show on POAP as have 2 transactions. Some POAP apps like Salsa no longer show the same connections after doing this. I think that is fine, but it is worth noting.
It was less simple with Nifty Ink since I was moving over 730 NFTs. uNFT Wallet refused to even try and move all of them in one go, and there wasn’t a way to select 100 NFTs at a time. So I had to click groups of 60-90 of them and do a transaction each. After doing several of these, there were a handful of stragglers left that I actually used Nifty Ink to send to the other wallet. They are now all in niftyink.thingelstad.eth! 🎨
Thanks uNFT Wallet
There is no way I could have done this without a bulk tool like uNFT Wallet. It was an easy choice to buy one of their Limited Edition supporter NFTs to help support the project.
Isolating Crypto Assets and Access
For the last couple of years I’ve done all of my Ethereum activities using my thingelstad.eth address with the associated identity. I’ve used this for storing value, holding NFTs, collecting POAPs, and everything else. I decided that it was time to create some isolation of access and identity.
I’m still using thingelstad.eth as my primary address and means of authenticating with various services. It also holds a number of my NFTs and crypto assets. But I’ve also now created two activity-specific addresses.
mint.thingelstad.eth is the address that I’m using specifically just to mint NFTs. When you mint NFTs you have to authenticate with a new smart contract and usually provide some form of limited access to your assets. By using a dedicated address just for minting I can limit the risk of a malicious smart contract.
vault.thingelstad.eth is the reverse of the minting address. This address is specifically to hold NFTs or other assets that I have no intent of selling or transferring. This address will never be used to authenticate to any website. All activities here will be done using wallet transfers.
Additionally, I decided to create some specific addresses for applications that I use a lot. This was inspired in part from Vitalik’s conclusion:
That said, it is my view that wallets should start moving toward a more natively multi-address model (eg. creating a new address for each application you interact with could be one option) for other privacy-related reasons as well.
I love the idea of wallets automatically associating a unique address with each application. I do this today by using a masked email addresses with Fastmail and passwords managed by 1Password.
ens.thingelstad.eth is the address I’m using to hold my Ethereum Name Service registrations. ENS has built in capability for one address to register a name, and the control of that name to be delegated. So all of my 21 registered ENS names are now owned by this address, and control of them is delegated to thingelstad.eth. The only app that will ever connect to this address is ENS itself, which protects my name registrations from malicious actors.
POAP.thingelstad.eth is an address I’ve made just for collecting POAP tokens. I currently hold 90 different POAP tokens in this address. This allows me to have a specific identity and address just for POAP usage. Most activity for this address is on Gnosis Chain since that is what POAP uses natively.
niftyink.thingelstad.eth is an address just for using Nifty Ink. I’ve collected 736 “inks” on this site and now I have them isolated into an address that I only use for that purpose. 🤩 This is again a way to limit access from a malicious smart contract.
Technically I also have reddit.thingelstad.eth but was created by necessity since Reddit Vaults are managed differently. However, it serves the same pattern as the other application specific addresses.
POAP 6390435 at SPS TechConnect 2023 Speaker.

POAP 6366384 at SPS TechConnect 2023.

I minted Cat #2230 of the Ukraine Cats Division. This NFT project is raising funds to help Ukraine defend itself. I think I’ll mint a few more and get a Ukraine Cat Platoon going. 😸🇺🇦

MnTech Leadership Forum: Generative AI
Today I hosted the MnTech Q1 2023 Tech Leadership Forum. The organization is changing the format of this event to have technology leaders run these quarterly forums. I thought it would be fun to focus on the topic that is making so much press lately — Generative AI: Harnessing Disruption into Innovation.

I was lucky enough to get three others to join in the dialog:

Some of the topics discussed:
Since it was an invite only event for members there isn’t a video to share. 😕

Of course there is a POAP for the event! And even more exciting, the POAP is also held by POAP.MnTech.eth which is the first POAP that MnTech is officially producing.
I Adopted Thinking Face Emoji
I ran across this Adopt a Character campaign from the Unicode Consortium and felt like a donation made sense. But what emoji to pick? After thinking through a few I decided Thinking Face. 🤔

This is fun, but I think it would be so much cooler if this program worked by selling NFTs. It has all the right characteristics with Gold and Silver levels being limited, and Bronze being “open editions.” It would be really fun to have this in my wallet as proof of participation.
POAP 6315996 at Thingelstad Valentines Day 2023.

Extending the Minnestar Community Supporter Program
In a recent conversation with Minnestar Executive Director Maria Boland Ploessl I was very pleased to hear about the amazing growth of the Minnestar Community Supporter program. Community Supporters were something that we launched when I was on the board of Minnestar to create an opportunity for individuals to support Minnebar and Minnedemo, in addition to companies. It was always significant, even on the first year, but it has grown a lot in recent years. The biggest part of that growth has been the structured year-end giving program which I was happy to be a matching supporter of this year.
The growth is awesome, but the program itself hasn’t changed materially since the launch. The primary benefit of being a Community Supporter is that you are guaranteed a ticket to the highly in-demand events that Minnestar hosts. That is a great benefit, but I’ve always wondered what more could be done for this great group of people that are helping support our technology community. Particularly what could be done outside of events.
In my opinion, being a Community Supporter of Minnestar should be table stakes for any technology leader in the region. It should be the most direct way to give back to the technology community we are all part of, and provide meaningful value to the supporter individually. I think supporting the events and community is solid, but the only meaningful value to the individual is a guaranteed ticket.
So what more could be done to grow the program? Some ideas…
Create Connection
People that become Community Supporters are a pretty special and fun group. Creating more connection in that group could be incredibly valuable. This could be done with in two phases.
First, launch an every-other week newsletter just for Community Supporters. This newsletter could include:
The newsletter could be the whole thing, but if there is an increase in engagement a forum for Community Supporters could get traction. I specifically do not mean Slack or Discord. Those are far too high engagement. A platform like Discourse seems much better suited to this. I think Minnestar could benefit from a Discourse like platform for everything, with Community Supporters being a member only section.
Membership
There needs to be more ways to show a persons affiliation with Minnestar, and recognize that support. I’ve been a Minnesota Public Radio member since 1995. How do I know that? My member card says it. I’ve been an Electronic Frontier Foundation member since 2010. It’s on my member card.
First step of this should be to issue an actual Minnestar Community Supporter member card. Cards have to be printed, they expire, etc. There is effort to do this but it gives me something to carry with me and show my membership.
This should also be extended into the digital world with POAP tokens. There should be a POAP for each year given to community supporters. Over the years, you collect each yearly POAP.
This would also be an opportunity to highlight the work of a local artist and create a uniquely designed card and token each year that isn’t just membership, but something that people feel like collecting.
I’ve been a Community Supporter member since the program started, but I have no idea how long that has been!
Input & Direction
Community Supporters as a group could be given the opportunity to have input on Minnestar activities. As a group votes could be taken. Thought would have to be given on what the votes are on. There is a Minnestar Board and various committees, and they should continue to do what they do. But there could be decisions that the community supporters are asked to give a vote on.
I had long thought that it would be really great for one of the Minnestar board seats to be a Community Supporter seat. In this case, the Community Supporters would elect amongst themselves one member that would represent them on the board. This could be facilitated via the forum above, with members raising their hands to serve and make their case followed by an official voting period.
This would lend itself exceptionally well to a Minnestar DAO, with membership gated via the Community Supporter POAP that you receive each year.
Ecosystem Benefits
It would be interesting to explore ways that other organizations in the technology community may want to extend benefit to Community Supporters of Minnestar. This is one of the key reasons to create Membership with a card and a token. Perhaps Twin Cities Startup Week would offer some unique opportunity. Or Tech.MN give a discount on membership. Or early access to certain events.
This would require that Minnestar reach out to have conversations around this with other events, and require proof of being a Community Supporter without access to Minnestar resources. I think this could work, and may be welcome from other organizations as well.
Art Shanty Projects
We went to the Art Shanty Projects on Lake Harriet today. Tammy has been to this many times, but it was my first. I do like events like this that make for fun days in the cold of winter. The Shanties themselves were very cool. Notable highlights:
I was left wanting to have a Shanty next year that distributed a POAP and allowed people to record a memory of the event in some way. 🤔





Echo Forest Launch
Today is the launch of Echo Forest. This NFT project has Minneapolis connections being led by Brooks Clifford and Matt Benesch.
I minted two Wolf Healers, 18 and 19. I really dig the artwork and I’m excited to see how the utility evolves. Plus it is a great opportunity to be involved in a local project.


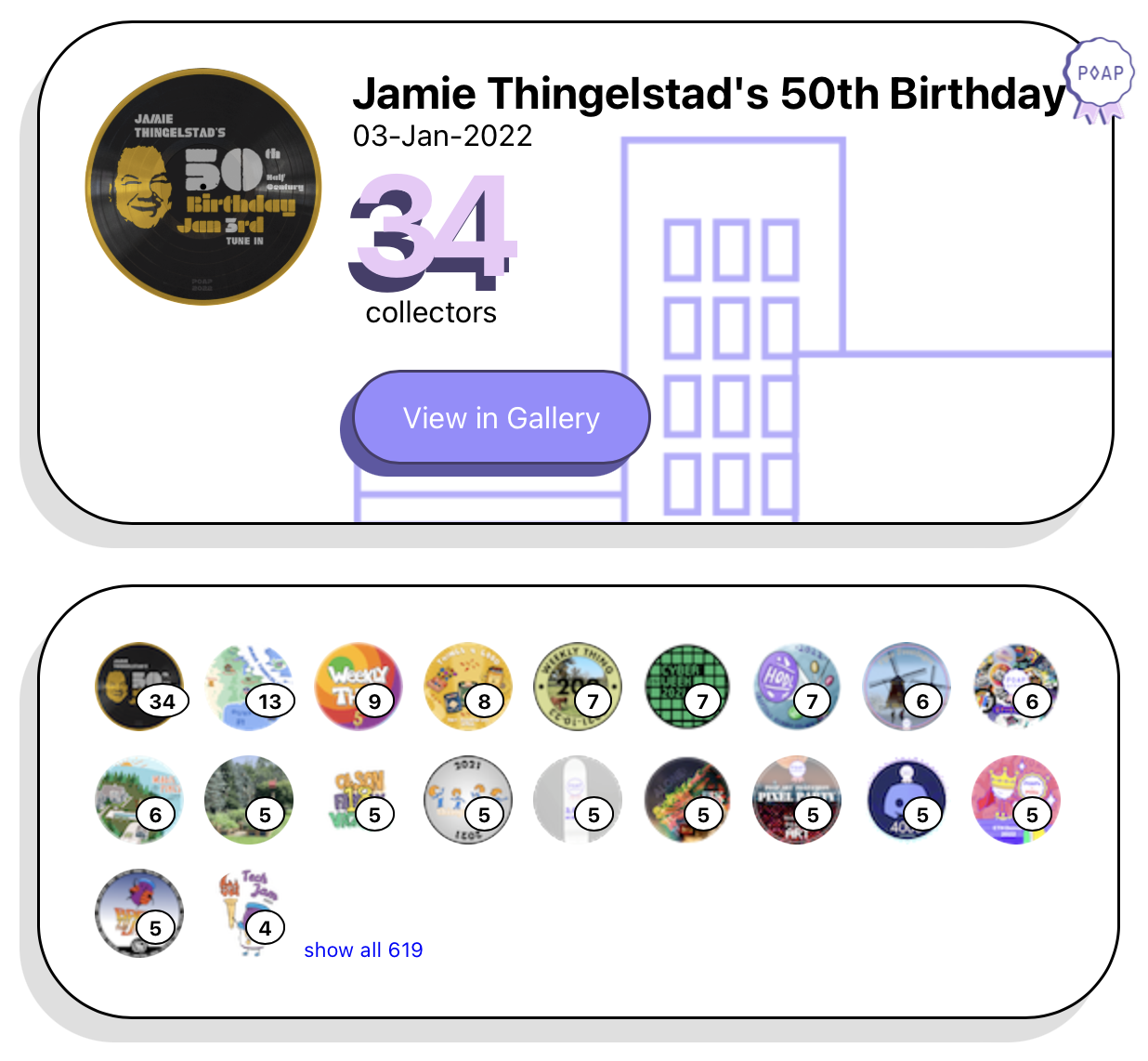
POAP Family
The new POAP Family feature is a cool way to see what POAPs people share between events. I looked at holders of my 50th Birthday POAP and I was surprised to see that there were 7 Cryptog’s HODLER’s who had my birthday POAP. The biggest were 13 of the 34 that also had my 51st Birthday POAP.
This kind of graph analysis of POAPs is an interesting extension and a way to build connection.
POAP 6261374 at TeamSPS 5th Floor Grand Reopening.

POAP as a Business
POAP is more than just a fun crypto product, it is also a business. I put some brief thoughts together on what I thought would be a POAP product that I would pay for as both a collector and an issuer.
As a POAP collector, I would want to pay a relatively small monthly fee to be able to get cool information about my collection and display it well.
POAP Collector - $3/mo
Now, changing hats to the issuer side there are a whole different set of things. What if we just kept everything as is, but added a new POAP Pro level.
POAP Pro - $20/mo
I think you could then have a service to provide a “full service” experience for the issuer.
POAP Studio - $500/event, require Pro subscription
And then you could turn both the Pro and Studio option into a subscription offering.
POAP for Business - $100/mo or $1,000/yr
And lastly, I think non-profits could be a really great avenue to get the word out about POAP. Aligning with non-profits would reach a very solid set of organizations that could benefit from POAP, and be a wonderful brand alignment with POAP itself. Make it super cheap or free for non-profits to use advanced POAP Pro and Studio capabilities.
POAP for Non-Profits - $20/mo or FREE




